Towards a framework for assessing systemic cyber risk
Published as part of the Financial Stability Review, November 2022.
Digitalisation is transforming the global economy, including by raising productivity and broadening consumer access to information. While these forces are facilitating greater competition, supporting economic growth and lowering prices, the benefits are not without risks – the flip side of digitalisation can be greater vulnerability to cyberattacks. For these to be a source of risk to financial stability, substitutability, risk correlation and interconnectedness are all key dimensions. A cyberattack on a critical infrastructure or an attack on one service that unearths vulnerabilities in another could quickly lead to system-wide stresses. Negative externalities arising from the effectiveness of financial institutions’ management of cyber risk could provide grounds for a public policy response. While the existing macroprudential policy toolkit has limited capacity to address cyber risks, their growing relevance nevertheless calls for macroprudential overseers to anticipate them, assess the capacity of the financial system to absorb them, and to issue risk warnings when warranted. In this vein, econometric evidence suggests that cyberattacks are not random, but are driven by factors such as economic strength, the degree of financial globalisation as well as policy and political uncertainty. This underscores how important it is for authorities to foster the sharing of information and the closing of data gaps on cyberattacks.
1 Introduction
Cyberattacks are becoming more frequent and severe. In tandem with rising global digitalisation, and the waxing and waning of geopolitical risks and economic uncertainty, the number of cyberattacks reported in 2021 was around three times larger than the figure for 2015, before falling back somewhat after that (Chart C.1, panel a). At the same time, public interest in and awareness of the problem has risen substantially (Chart C.1, panel b).[1] While digitalisation has helped to boost productivity and facilitate greater competition in markets for goods and services, the benefits are not without risks – the flip side of digitalisation can be greater vulnerability to cyberattacks as reliance on digital infrastructures increases. For instance, cloud technologies centralise information and data storage while also creating interdependence through greater network traffic. This increases the number of routes available to launch opportunistic and targeted cyberattacks. While the recent peak of cyberattacks coincided with the adoption of social distancing measures during the coronavirus (COVID-19) pandemic, the subsequent decline should not be a cause for complacency. Arguably, the most likely long-term outcome is broader and deeper digitalisation of economic and financial activity, meaning that vulnerability to cyberattacks can only be expected to rise as well. Consistent with this, and notwithstanding uncertainty, analyst estimates of the cost of cybercrime have climbed, underpinning expectations of substantial growth in the cybersecurity industry (Chart C.1, panel c). Against this background, this special feature examines whether and to what extent risks stemming from cyberattacks have the potential to undermine the stability of the financial system.[2] It investigates the nature and sources of the increase in cyberattacks and considers whether frameworks commonly used for identifying, assessing and prioritising sources of financial stability risks and vulnerabilities are sufficiently flexible to accommodate cyber risks.[3]
Chart C.1
Both cyberattacks and public interest in cyber risks have risen markedly in recent years, while significant growth of the cybersecurity industry is expected

Sources: University of Maryland CISSM Cyber Attacks Database, Google Trends, Statista, financial statements of key players, national cybersecurity organisations, IMF, World Bank, UN, Eurostat and ECB calculations.
Note: Panel b: the Google trends shown here are measured as an index which takes the value 100 for the point of highest search interest for any of the three terms since 2004. Panel c: data, including estimates and projections, are provided by Statista. Market sizes are determined based on the annual financial statements of market-leading companies and industry associations, national statistical offices and specific countries’ security organisations. Forecasts use different methods, such as exponential trend smoothing and the autoregressive integrated moving average (ARIMA) models. The main drivers are GDP, internet users, level of digitisation and consumer attitudes towards data and IT security. Data are modelled using current exchange rates.
2 Financial stability implications of cyber risks
Digitalisation is creating economic and financial interlinkages that warrant taking a macro-financial perspective on cyber threats. It is commonly accepted that there are two key dimensions to systemic risk: one is cross-sectional and the other time-related.[4] The cross-sectional dimension concerns the distribution of risks within the financial system at any given point in time and how specific shocks to the financial system can propagate themselves and become systemic. Among other things, it relates to the size and interconnection of financial institutions and markets and the capacity for contagion through factors like direct or perceived exposures to troubled institutions. The time dimension encapsulates the endogenous evolution of financial stability risks over time, including cumulative and procyclical build-ups of financial fragility in the boom phase and excessive risk aversion – and even runs – in the bust phase.
Chart C.2
All economic sectors have direct or indirect exposure to cyber risks and complex interconnections can lead to cascading effects
Schematic overview of sectoral exposure to cyber risks
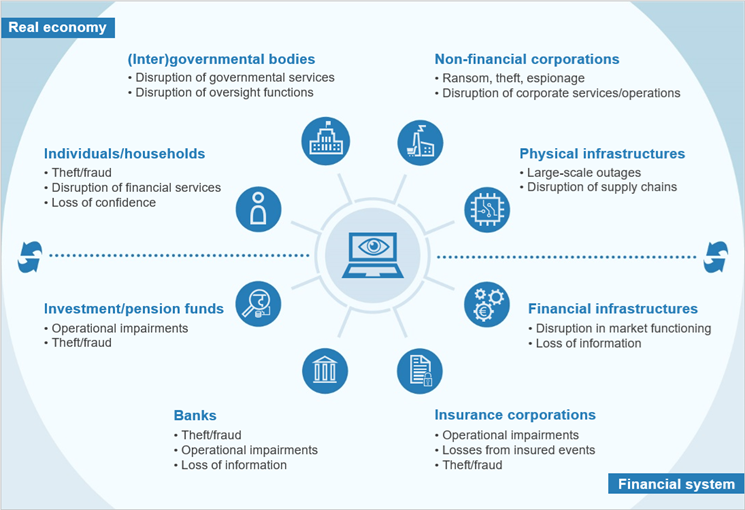
Source: ECB staff.
The relevance of cyberattacks has been evolving across both the cross-sectional and the time dimension of systemic risk. Regarding the cross-sectional dimension, rapid financial innovation and digitalisation is increasing the susceptibility of both financial and non-financial sectors to cyberattacks (Chart C.2). As interlinkages between real and financial activities increase, the potential grows for cyberattacks originating in the real economy to spread and create operational challenges for financial institutions. For instance, supply chain disruptions or power outages could result in operational difficulties for the financial sector, given its financial or technological dependence on real economy agents. Moreover, cyber risks emanating from the real economy could easily spill over to the financial sector, impair financial intermediation and feedback more broadly to the real economy, and vice versa. Accordingly, any discussion of the financial stability implications of cyberattacks requires taking a holistic macro-financial perspective.
Chart C.3
Cyberattacks could pose a systemic risk to the financial system given their potential to disrupt critical financial services and operations
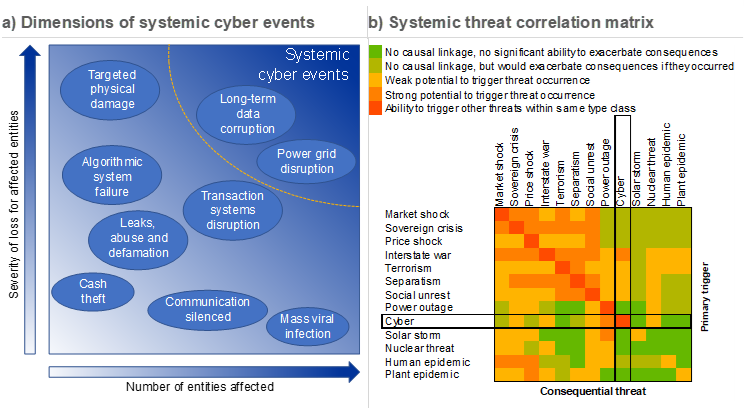
Sources: ESRB, Cambridge Centre for Risk Studies and ECB.
Notes: Panel a: adapted from ESRB, see footnote 6 for full reference. Panel b: adapted from Table 3 in Cambridge Global Risk Index 2017, Cambridge Centre for Risk Studies, University of Cambridge, 2016.
Cyberattacks can have systemic consequences if a critical entity is affected or if interlinkages between multiple affected non-critical entities cascade into systemic threats. Arguably, the increased digital reliance of virtually every aspect of economic, financial and social activity has created a necessary – but not sufficient – condition for cyberattacks to become a systemic risk. Contained cyberattacks that only affect single firms are only problematic in cases where the victim is a systemically important entity. For non-systemic entities, cyberattacks are theoretically only problematic for the firms affected, but interlinkages between the different entities can lead to cascading effects where the potential for systemic threats becomes greater when critical infrastructures are affected.[5] Within the financial system, operational, financial and confidence channels can amplify the impact of a cyberattack to the point where they impair the provision of key economic functions.[6] The potential for cyberattacks to become sources of risk for financial system stability depends on how widespread and how severe the loss impact is (Chart C.3, panel a). Furthermore, substitutability, risk correlation and interconnectedness are all key dimensions in determining systemic relevance. For instance, a cyberattack on a critical infrastructure that cannot be easily replaced, or an attack on one service that unearths vulnerabilities in another, could quickly lead to system-wide stresses. Likewise, cloud technologies centralise information and data storage while also creating interdependence. As reliance on these services increases, so too does the potential for cyberattacks that could paralyse economic and financial activity (Chart C.3, panel b).
3 Gauging the threat environment
Shortcomings in data availability, as well as quality issues, pose challenges for the quantification of both the likelihood and the possible impacts of cyberattacks. For the victims of cyberattacks, issues such as business reliability, as well as management credibility and reputation, are likely to determine decisions about reporting, and specifically what to report. This means that the information on the scale, scope and features of cyberattacks that is shared publicly is only partial and is likely to contain selection biases. By providing open-source information on publicly acknowledged cyberattacks on private and public organisations across the globe, the University of Maryland’s CISSM Cyber Attacks Database[7] nevertheless offers some insights into the nature of cyberattacks. It covers around 9,700 of such incidents between 2014 and 2022.[8]
The number of publicly-known cyberattacks has increased markedly in recent years, with the bulk of these events clustered in the major advanced economies. Growing continuously since 2014, the number of reported incidents reached what is likely to prove a temporary peak in 2020 during the pandemic, when many service-oriented sectors switched to remote working modalities, opening up new opportunities for attackers while, at the same time, increasing vulnerabilities. According to the dataset, developed economies have fallen victim to cyberattacks more frequently than developing economies, with over 50% of the cyberattacks in the database having been recorded in the United States, while euro area countries account for around 13% (Chart C.1, panel a).
Chart C.4
The characteristics of cyberattacks differ across economic sectors
Breakdown of global cyberattacks by sector, event type, threat actor and motive
(2021, percentages)

Sources: University of Maryland CISSM Cyber Attacks Database and ECB calculations.
Criminals with financial motives are the dominant force driving cyberattacks, but actors and motives differ across economic sectors. Public administration, health care and education are the most frequently targeted economic sectors. Attacks on the financial sector are more moderate, accounting for around 5 to 10% of the total (Chart C.4). Over 40% of the attacks on the financial sector reported in 2021 were exploitive in nature[9], which is more than was the case for other sectors; manufacturing, education and public administration, for instance, have been more often targeted with disruptive intent. On aggregate, most attacks are carried out by criminals, and this is also the case for the financial sector where more than 90% of cases involved criminals. Other actors who have primarily targeted the financial sector, IT and public administration, include hacktivists[10] and nation-states. While financial motives – accounting for over 75% – are the dominant driver of attacks on the financial sector, protests also play a role. The IT sector and public administration, and manufacturing and professional services, are also targeted with political and industrial sabotage intent respectively.
Drivers and implications of cyber risks
Cyberattacks do not occur randomly, but rather reflect identifiable factors including economic strength and the degree of financial globalisation. At the country level, the frequency of cyberattacks seems to coincide with economic importance, measured by country shares in global GDP. To the extent that the degree of digitalisation is a function of economic progress, this may influence the ways and means of carrying out cyberattacks. At the same time, financial motives may go hand-in-hand with economic progress. Similarly, a country’s degree of integration into global financial structures also appears to play a role, highlighting the systemic potential of cyberattacks (Chart C.5, panel a).
Chart C.5
Economic strength, the degree of financial globalisation as well as political and policy uncertainty may explain the frequency of cyberattacks
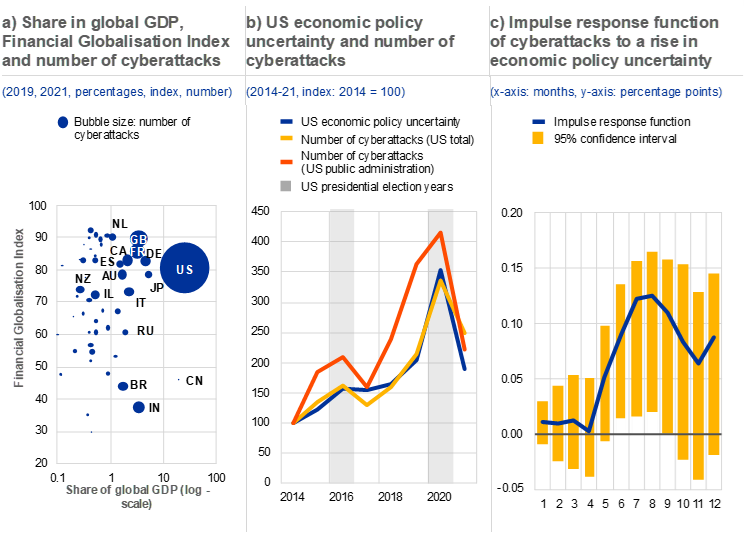
Sources: University of Maryland CISSM Cyber Attacks Database, KOF Swiss Economic Institute, policyuncertainty.com and ECB calculations.
Notes: Panel a: for the Financial Globalisation Index, the latest figures referring to 2019 are used; see Dreher, A., “Does globalization affect growth? Evidence from a new index of globalization”, Applied Economics, Vol. 38, Issue 10, 2006 and Gygli, S., Haelg, F., Potrafke, N. and Sturm, J., “The KOF Globalisation Index – revisited”, Review of International Organizations, Vol. 14, 2019. The share of global GDP and the number of cyberattacks refer to 2021. Panel b: US economic policy uncertainty shown here is the annual average of monthly data. All data in this chart are indexed to their 2014 value at a level of 100. Panel c: the chart shows an impulse response function for a one percentage point economic policy uncertainty shock on the log-difference in cyber incidents based on a vector autoregressive (VAR) model using data on global policy uncertainty and global cyber incidents, and including dummy variables preceding the 2016 and 2020 US elections.
In addition to these cross-sectional factors, there is evidence that cyclical factors such as policy uncertainty play a role as well, so that the occurrence of cyberattacks appears to have a time dimension as well. For instance, the frequency of cyberattacks tends to increase at times of heightened political and policy uncertainty – such as during the months preceding US presidential elections – as well as at times of geopolitical tensions (Chart C.5, panel b). This seems to be particularly the case for state-sponsored attacks, which have grown in recent years together with the escalation of geopolitical conflicts, with the bulk of events aiming at espionage and sabotage in the public sector. Econometric tests for Granger causality show that policy uncertainty may partly explain the frequency of cyberattacks, but not vice versa.[11] More specifically, an increase in policy uncertainty tends to be followed by a rise in the frequency of cyberattacks in the subsequent six to nine months (Chart C.5, panel c).
Despite the increasing frequency of cyberattacks, there is only limited granular data on the economic losses associated with reported attacks. If the cyberattack is successful, the costs for affected firms can take a variety of forms. Some costs, like a ransom paid to a threat actor, are clear, at least to the victim. At the same time, a loss of revenue – due to service interruption, reputational damage, loss of customer trust or loss of competitiveness from intellectual property theft, for instance – may have a financial impact that is hard to measure. Costs can also be imposed on third parties, such as when stolen credit card data are used fraudulently. Estimates for the aggregate costs of cybercrime are available from various sources, yet the exact costs per cyberattack are only disclosed for around 5% of global cyberattacks, with the amounts involved averaging around USD 13 million.[12] The bulk of the costs appear to be concentrated in only a few sectors (Chart C.6, panel a), while the distribution of costs related to cyberattacks is highly skewed in some sectors. In particular, for several cases in the financial sector, the costs were large multiples of the average. But these cases only represent those attacks which have financial motives. Although these types of attack are the most common, the losses that come with other types of cyberattack, such as corporate espionage or sabotage operations, could have much larger pecuniary impacts and more severe consequences for financial stability. Within the euro area banking system, financial impacts are partly absorbed by capital charges based on Pillar 2 requirements for operational risk, of which cyber risk is a subgroup.
Not only are crypto-assets the dominant method of payment in response to cyberattacks, but a substantial share of such attacks involves the theft of crypto-assets. For the financial sector, more than two-thirds of the total costs can be attributed to the theft of crypto-assets, for example, due to attacks on crypto-exchanges, wallets and decentralised finance platforms (Chart C.6, panel a). Since crypto-assets are the payment method most frequently reported in cases of fraud, cyberattackers appear to value the anonymity of this asset class.[13] This seems to suggest that the rise of crypto-assets[14] may have contributed to the rise of cyberattacks over recent years.[15]
Chart C.6
The bulk of costs related to cyberattacks are concentrated in a few sectors, but investment in IT safety precautions can lower related costs
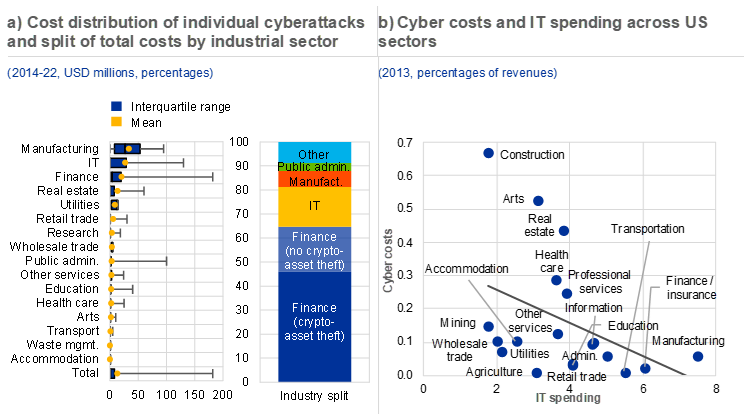
Sources: University of Maryland CISSM Cyber Attacks Database, Aldasoro et al. and ECB calculations.
Notes: Panel a: the left graph shows the cost distribution of individual cyberattacks across industrial sectors. The sample size in some sectors is small and hence the results should be interpreted with caution. The right graph shows how the total costs of cyberattacks are allocated across industries. The financial sector cyber costs are split further, based on whether crypto-assets are stolen. Cyberattacks with large outliers in terms of their costs were excluded. Panel b: the InformationWeek500 (IW500) dataset provides an estimate of firms’ IT expenditures as a percentage of revenues (revenues × IW500 measure); the IW500 survey was last carried out in 2013. The survey gathers data on IT spending from 500 US-based firms across various sectors. See Aldasoro, I., Gambacorta, L., Giudici, P. and Leach, T., “The drivers of cyber risk”, Journal of Financial Stability, Vol. 60, June 2022, and Kennedy, D. and Stratopoulos, T., “Mapping IT Spending Across Industry Classifications: An Open Source Dataset”, SSRN, November 2017.
Investment in IT safety precautions can lower the costs of cyberattacks. As a proportion of revenues, cyberattack-related costs in the US tend to be highest for the construction and arts industries, while the finance and insurance industry faces relatively low costs compared to its revenue. Some research indicates that the costs of cyber incidents are inversely proportional to IT spending; in other words, when IT spending increases, the costs relating to cyberattacks decrease (Chart C.6, panel b).[16] However, despite this potential mitigant, systemic risks can still arise when a financially weaker but systemically relevant actor is successfully targeted. As such, vulnerabilities ultimately cluster around targets at the intersection of high technological dependence, weaker financial resilience and low awareness.
Chart C.7
Cyber insurance premiums have increased significantly as the frequency of cyberattacks have multiplied, while rating agencies started to factor in cyber risks
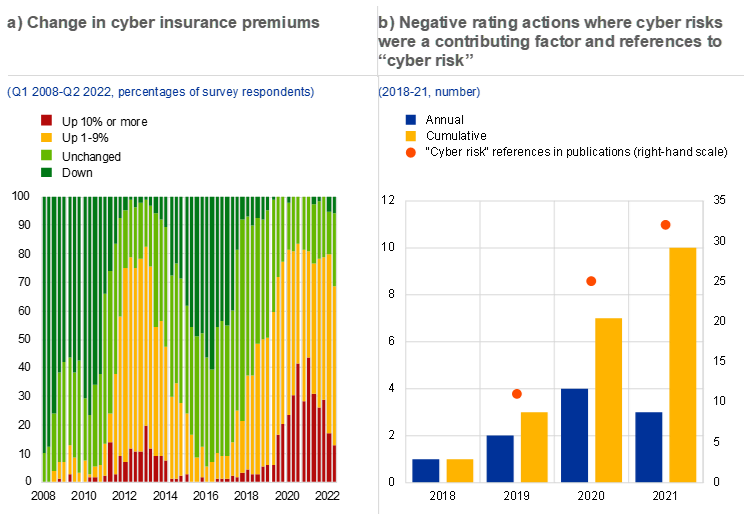
Sources: Bloomberg Finance L.P., The Council of Insurance Agents & Brokers, S&P Global Ratings and ECB.
Notes: Panel a: answers of “do not know” or “not applicable” are excluded. Panel b: data refer to rating actions and company publications by S&P Global Ratings.
Heightened risks of cyberattacks have increased global demand for cyber insurance, and there are nascent signs of rating downgrades resulting from cyber incidents. So far, cyber insurance remains a niche segment mainly concentrated in the United States. However, with the increasing frequency of cyberattacks over the last decade, non-financial firms’ demand for insurance against cyberattack-related losses has risen commensurately. This has, in turn, pushed insurance premiums sharply upwards (Chart C.7, panel a). For instance, US insurance rates increased by 27% in the second quarter of 2022 compared to the previous quarter. Insurers cite systemic exposures and accumulation risk – including the risks resulting from the Russian invasion of Ukraine – as potential significant loss-triggering events.[17] At the same time, rating agencies have started to incorporate cyber risks into the social pillar of their ESG scores. Over recent years, cyber risk has increasingly featured in rating agency publications and has already resulted in some negative rating actions (Chart C.7, panel b).[18]
5 Policy considerations
Informational asymmetries, as well as the concentration of risks and externalities, could result in a failure of markets to optimally price the risks associated with cyberattacks. Cyber risks feature a set of characteristics which complicate the implementation of potential mitigants. Information asymmetry induces the risk that entities take on risks while knowing they will not be forced to bear the full costs when they fall victim to a cyberattack (moral hazard) and the risk that only weaker entities insure themselves (adverse selection problems), which in turn can undermine market functioning.[19] For instance, the reporting of cyber incidents implies documenting cyber vulnerabilities, which could translate into higher insurance premiums, higher debt funding costs and lower credit ratings, creating so-called agency problems associated with informational asymmetries. Moreover, losses resulting from specific types of cyberattack become uninsurable and are excluded from cyber insurance policies.[20] Exclusions might result in large financial losses in the event of a systemic attack, when insurance is truly needed. Public policies – aimed at addressing market failures and externalities – could therefore help in ensuring resilience against systemic threats.
As risks have increased, regulatory bodies have been designing and operationalising frameworks that seek to mitigate cyber risks. To the extent that more knowledge is gained about the fundamental drivers of cyberattacks, it becomes easier to foresee potential vulnerabilities and adjust action accordingly. In recent years cyber awareness has increased markedly in the public domain, including in central banks. At the same time, research shows that cyber threats can be mitigated by increasing IT spending on preventive measures. However, as the sophistication of IT security technology evolves, so too can it be expected that the technology deployed by cyberattackers will respond, creating a dynamic resembling that of an arms race. Ultimately, trade-offs are likely to be faced between the costs imposed by cyberattacks and ever-increasing spending on security measures. Especially when the threat actors are state-backed, the resources required to fend off attacks may be too onerous for single firms to shoulder. Arguably, defence against such threats should fall under the purview of national security forces.
Different international fora are also working on initiatives to promote cyber resilience. For instance, the G7 Cyber Expert Group is working on third-party risk, threat-led penetration testing and cyber exercise programmes. The Financial Stability Board has compiled a cyber lexicon to achieve a common vocabulary and proposed a cyber-incident response and recovery toolkit, and the Committee on Payments and Market Infrastructures at the BIS has issued cyber resilience guidelines for financial market infrastructures. At the European level, microprudential supervisors have included cyber risks in their supervisory priorities[21] and introduced a cyber-incident reporting framework to monitor threats that significant institutions are facing. On the macroprudential side, the European Systemic Risk Board (ESRB) has recommended the establishment of a pan-European systemic cyber-incident coordination framework to mitigate the risk of coordination failure[22]. Finally, the EU’s forthcoming Digital Operational Resilience Act will put in place a detailed and comprehensive framework on digital operational resilience for EU financial entities, with the aim of strengthening cybersecurity in financial services and addressing broader operational risks.
6 Conclusions
Macroprudential authorities are developing frameworks to monitor and identify systemic risks stemming from cyberattacks, but momentum is essential in a rapidly evolving risk landscape where data gaps exist. Three key messages emerge from the analyses set out in this special feature. First, cyberattacks have a cross-sectional dimension. They can pose systemic risk if they affect a critical entity or if interlinkages between multiple affected non-critical entities cascade into systemic threats. Second, threats originating from cyberattacks also have a time dimension. Such threats seem to increase in periods of heightened political and economic uncertainty. The data used in this special feature indicate that developed economies have fallen victim to cyberattacks more frequently than developing economies, likely reflecting the stage of digitalisation that economies have reached. Finally, although the existing macroprudential policy toolkit has limited capacity to address cyber-related risks, there is much that macroprudential supervisors can do to monitor and assess the risks. Econometric evidence shows that, rather than being random and idiosyncratic, systematic patterns in cyberattacks can be linked to both economic and political cycles. Large data gaps, a fast-changing cyber landscape and the complexity of systemic cyber risks as well as growing interlinkages between technologies and the financial system make it challenging to design policies tailored to mitigate risks associated with cyberattacks. As such, policymakers should work to improve monitoring and analytical frameworks, expand the macroprudential toolkit and foster collaboration and information-sharing at both operational and policy levels to increase and safeguard resilience of the financial system and mitigate the systemic impact of cyberattacks.[23]
See, for instance, European Risk Manager Survey Report 2022, Federation of European Risk Management Associations, 2022.
The term “cyberattacks” refers to cyber incidents that are due to deliberate human action, usually with malicious intent. According to the Financial Stability Board’s cyber lexicon, the term “cyber incidents” refers to cyber events that compromise the cybersecurity of an information system or the information the system processes, stores or transmits or violates the security policies, security procedures or acceptable use policies. Hence, cyber incidents can also be caused by technological failures or accidental human errors. While the broader category of cyber incidents is as relevant to financial stability risks as cyberattacks, the discussion here focuses on the latter.
For a framework of financial stability analysis, see, for instance, Fell, J. and Schinasi, G., “Assessing Financial Stability: Exploring the Boundaries of Analysis”, National Institute Economic Review, Vol. 192, Issue 1, 2005, pp. 102-117. The term “cyber risk” refers to the combination of the probability of cyber incidents occurring and their impact.
See Borio, C., “Towards a macroprudential framework for financial supervision and regulation?”, BIS Working Papers, No 128, Bank for International Settlements, 2003.
See also the box entitled “Financial stability vulnerabilities stemming from cyber risks within financial market infrastructures”, Financial Stability Review, ECB, May 2016.
For a detailed framework of systemic cyber risk to financial stability, see “Systemic cyber risk”, ESRB, February 2020; and Ros, G., “The making of a cyber crash: a conceptual model for systemic risk in the financial sector”, Occasional Paper Series, No 16, ESRB, 2020. For a real-life example of such mechanisms in play, where, however, systemic spillovers were avoided, see Kotidis, A. and Schreft, S., “Cyberattacks and Financial Stability: Evidence from a Natural Experiment”, Finance and Economics Discussion Series, No 2022-025, Board of Governors of the Federal Reserve System, 2022.
See Harry, C. and Gallagher, N., “Classifying Cyber Events: A Proposed Taxonomy”, Journal of Information Warfare, Vol. 17, No 3, 2018, pp. 17-31.
While likely not fully representative of the true threat landscape, given cultural differences in the acknowledgement of cyberattacks across sectors or political systems, for instance, this still appears to be the most comprehensive publicly available database.
Exploitive attacks are those that illicitly acquire information, whereas disruptive attacks disrupt operations via denial of service or ransomware, etc. See Harry and Gallagher, op. cit. Among euro area significant institutions, phishing attacks accounted for the largest share of infection vectors in 2019, while denial-of-service attacks predominated in 2020. See “IT and cyber risk: a constant challenge”, Supervision Newsletter, ECB, August 2021.
The word “hacktivist” is a combination of “hack” and “activist”. It is used to refer to activists using hacking techniques to promote a political agenda.
Granger, C.W.J., “Investigating Causal Relations by Econometric Models and Cross-spectral Methods”, Econometrica, Vol. 37, No 3, 1969, pp. 424-438.
Just 5% of the cyber incidents covered in the CISSM Cyber Attacks Database include information on the costs. The term “cyber costs” used in this article captures a mix of total costs, partial costs (where part of the losses are recovered) and amounts initially demanded by attackers which might not necessarily lead to costs for the victim in the end.
See the Fraud Report published by the US Federal Trade Commission.
See, for example, the article entitled “Decrypting financial stability risks in crypto-asset markets”, Financial Stability Review, ECB, May 2022.
For a detailed discussion of crypto-enabled cybercrimes, see Cong, L.W., Harvey, C.R., Rabetti, D. and Wu, Z-Y., “An Anatomy of Crypto-Enabled Cybercrimes”, SSRN, October 2022.
See Aldasoro, I., Gambacorta, L., Giudici, P. and Leach, T., “The drivers of cyber risk”, Journal of Financial Stability, Vol. 60, June 2022.
See the Commercial Property/Casualty Market Index published by The Council of Insurance Agents & Brokers (CIAB) and Global Insurance Market Index Q2 2022 published by Marsh LLC.
Between 2019 and 2022, references to cyber incidents in S&P publications for non-financial corporate issuers increased by over 260%.
See Kopp, E., Kaffenberger, L. and Wilson, C., “Cyber Risk, Market Failures, and Financial Stability”, IMF Working Papers, No 2017/185, International Monetary Fund, 2017.
See “Cyber War and Cyber Operation Exclusion Clauses”, Lloyd’s Market Association Bulletin, No LMA21-042-PD, Lloyd’s Market Association, November 2021, also “EIOPA Strategy on Cyber Underwriting”, EIOPA, February 2020, and “Cyber risk for insurers – challenges and opportunities”, EIOPA, September 2019.
See “ECB Banking Supervision: SSM Supervisory Priorities for 2022-2024”, ECB, 2021.
See “ESRB recommends establishing a systemic cyber incident coordination framework”, press release, ESRB, 27 January 2022.
See also “Mitigating systemic cyber risk”, ESRB, January 2022.



